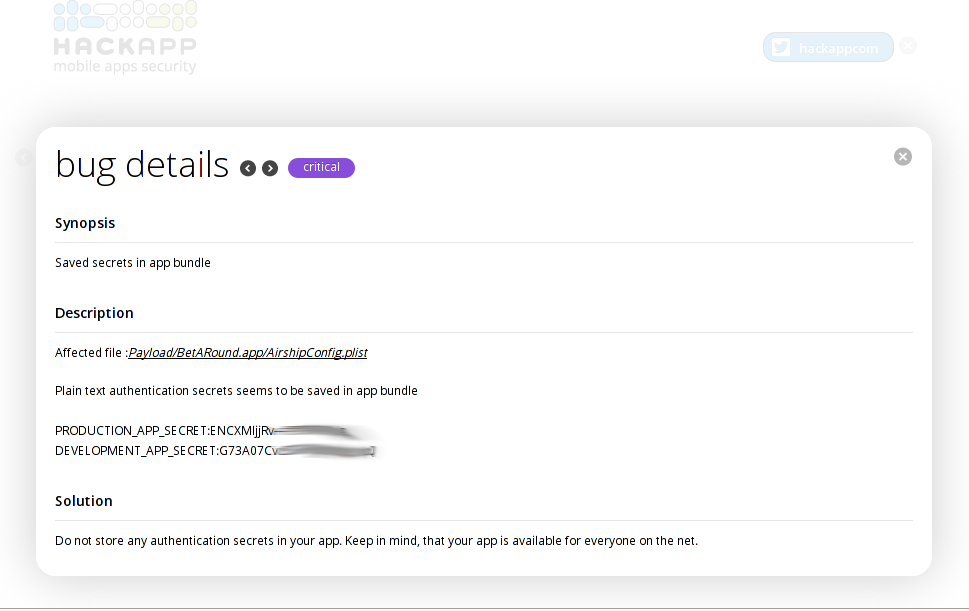
UPD: I've just received confirmation from Telegram, that a patched version was released a few hours ago. Here is the patch on github.
A few days ago Mr. Durov announced bug bounty for Telegram protocol decryption. Futher it will be shown how private data from a secret chat can be captured without any decryption methods due to a design failure.
Test environment:
- Android 4.3 launched in Virtual Box,
- Wireshark launched on host machine,
- HTC One with Android 4.0.3,
- Telegram 1.3.800 (in virtual box)
Method:
Let's install Telegram and create users Alice and Bob. After that, we are creating acconts in Telegram and adding each device to other's contact list.
Now we are starting a secret chat:
Sending a test message:
As we can see in wireshark - all data goes through SSL, and looks encrypted.
But what if we'll try to send attachment, for example a geolocation? Geolocations of secret chat members could be quit interesting in some cases :)? Let's tap 'send' button...
Bum!! We've got a clear-text TCP session! Let's take a look a bit closer..
Telegarm uses a default unencrypted google-maps API to resolve map snippet. From a security and anonimity point of view this is THE fail. It means that a person who controls the channel can capture all "geo-attachments" going through a secret chat in both ways (incoming and outgoing) using just a passive sniffer.
In practice, if Mr. Snowden will send his geo-location using Telegram to someone, who is under NSA wiretapping, a tomahawk will be enough to make Gen. Alexander satisfied.