What if I were a cloud? I guess many security engeneers have been asking themselves this question in recent days. In this post I want to share my vision of the most critical steps in cloud storage for mobile devices.
I do not claim an absolute correctness and there are no strict requirements, I wish this article could be a starting point for some technical discussions, while the topic is hot.
Baseline:
How it works step by step:
I do not claim an absolute correctness and there are no strict requirements, I wish this article could be a starting point for some technical discussions, while the topic is hot.
Baseline:
- Сryptography is unbreakable,
- Devices are equipped with TPM (trusted platform module),
- Attacker has no inconspicuous physical access to victim's device.
I know, that not all devices are equipped with a TPM chip (by the way, iPhone is equipped), but I heard, that SIM card can be used, as a TPM in some cases. If you know how it technically works, please let me know.
Enrollment
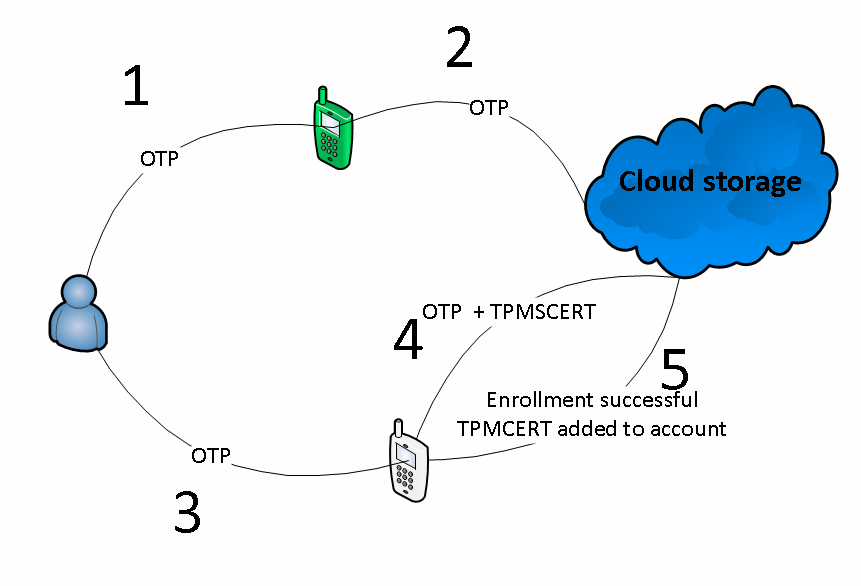
A new device enrollment is a critical step because Cloud should be sure that this device is authenticated and not a source of malicious activity. A device enrollment should be performed with two factor authentication. The second factor could be an OTP (one time password) sent as an SMS to the phone number associated with the account, or an OTP preset on any other device, which was already enrolled. For each new device the account owner should be notified by email.How it works step by step:
- User generates an OTP on a device enrolled previously;
- Generated OTP goes to cloud;
- User enters the OTP on a new device;
- Device generates a TPM signe Certificate request (TPMCRT);
- If OTPs from steps 2 and 4 are equal, the enrollment is successful.
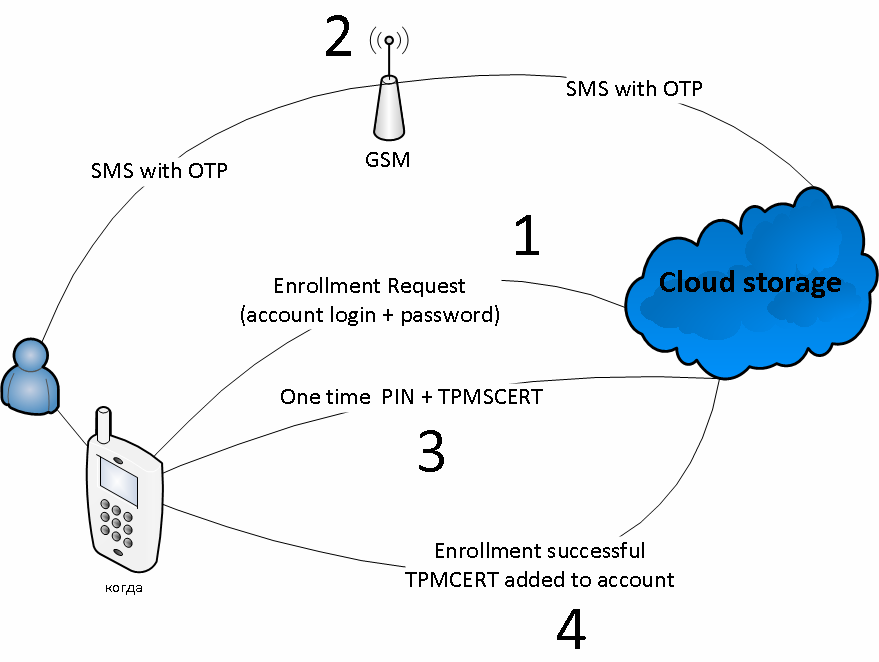
In the case of a new device:
- New device performs an enrollment request with a login and a password;
- Cloud sends SMS with an OTP to an associated phone number;
- New device sends TPMCRT + OTP;
- If OTPs from steps 2 and 3 are equal, the enrollment is successful.
What is TPMCRT :
- Client device generates a private key and a certificate request for each enrollment;
- TPM signs Certificate request (TPMCRT), so we get an unique device certificate.
Benefits:
- In a case of credentials leak, an attacker can't enroll a new device, and get user's data;
- If an attacker has an access to an enrolled device and can generate an OTP for a malicious device, the victim will get a notification.
Secure communication
First of all - certificate pinning, it should protect us from SSL MiTM. This kind of attacks could be a result not just of compromised Certificate Authority, using MDM mechanism, corrupt system administrators could distribute malicious Certificate Authority to devices, and then perform SSL MiTM.
Then Cloud should authenticate a device, in other words, Cloud should check that the device was enrolled:
- Device authenticates Cloud (with pinning);
- Device sends its certificate which was generated during enrollment.(?Https client-side authentication?);
- Cloud checks whether the certificate was enrolled;
- Cloud uses the TPM public key from the certificate and encrypts a CHALLENGE;
- Device receives the encrypted CHALLENGE and uses the TPM to decrypt it;
- Device generates a RESPONSE and encrypts it with the TPM;
- Device sends the encrypted RESPONSE to Cloud;
- Cloud decrypts it with the TPM public key, if it's ok, the authentication succeeded.
Benefits:
- TPM doesn't allow an attacker to gain access to Cloud, even if he or she was able to steal the private enrollment key (with a malware or forensic boot).
- We have the flexibility. For example, if we want to donate or sell the device, we can simply remove the enrollment key by device factory reset, or via Cloud web interface, if the device was stolen.
If you notice any mistakes or if you whould like to add anything, I will be happy to find your comment in Hackapp Facebook group or in any other place (plese leave link in comments).