What if I were a cloud? I guess many security engeneers have been asking themselves this question in recent days. In this post I want to share my vision of the most critical steps in cloud storage for mobile devices.
I do not claim an absolute correctness and there are no strict requirements, I wish this article could be a starting point for some technical discussions, while the topic is hot.
Baseline:
How it works step by step:
I do not claim an absolute correctness and there are no strict requirements, I wish this article could be a starting point for some technical discussions, while the topic is hot.
Baseline:
- Сryptography is unbreakable,
- Devices are equipped with TPM (trusted platform module),
- Attacker has no inconspicuous physical access to victim's device.
I know, that not all devices are equipped with a TPM chip (by the way, iPhone is equipped), but I heard, that SIM card can be used, as a TPM in some cases. If you know how it technically works, please let me know.
Enrollment
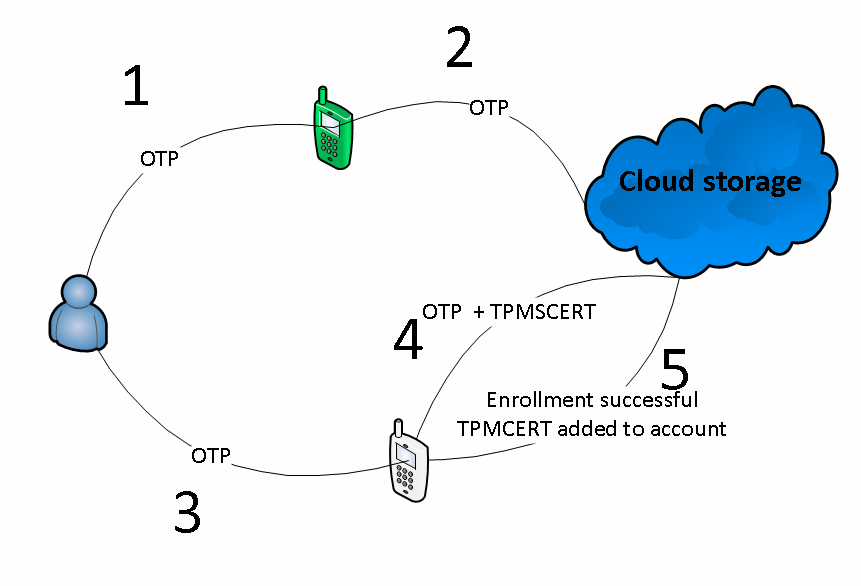
A new device enrollment is a critical step because Cloud should be sure that this device is authenticated and not a source of malicious activity. A device enrollment should be performed with two factor authentication. The second factor could be an OTP (one time password) sent as an SMS to the phone number associated with the account, or an OTP preset on any other device, which was already enrolled. For each new device the account owner should be notified by email.How it works step by step:
- User generates an OTP on a device enrolled previously;
- Generated OTP goes to cloud;
- User enters the OTP on a new device;
- Device generates a TPM signe Certificate request (TPMCRT);
- If OTPs from steps 2 and 4 are equal, the enrollment is successful.
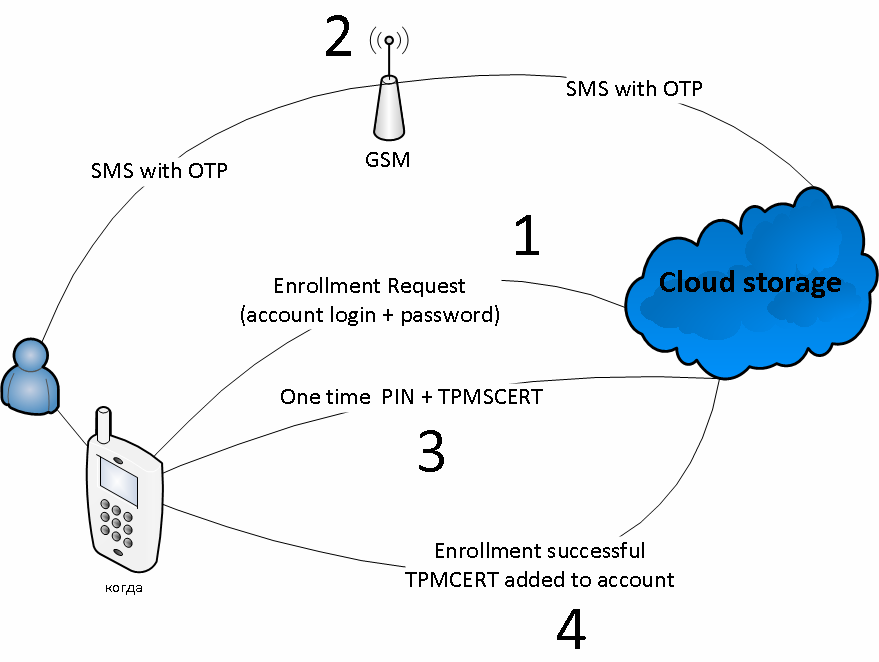
In the case of a new device:
- New device performs an enrollment request with a login and a password;
- Cloud sends SMS with an OTP to an associated phone number;
- New device sends TPMCRT + OTP;
- If OTPs from steps 2 and 3 are equal, the enrollment is successful.
What is TPMCRT :
- Client device generates a private key and a certificate request for each enrollment;
- TPM signs Certificate request (TPMCRT), so we get an unique device certificate.
Benefits:
- In a case of credentials leak, an attacker can't enroll a new device, and get user's data;
- If an attacker has an access to an enrolled device and can generate an OTP for a malicious device, the victim will get a notification.
Secure communication
First of all - certificate pinning, it should protect us from SSL MiTM. This kind of attacks could be a result not just of compromised Certificate Authority, using MDM mechanism, corrupt system administrators could distribute malicious Certificate Authority to devices, and then perform SSL MiTM.
Then Cloud should authenticate a device, in other words, Cloud should check that the device was enrolled:
- Device authenticates Cloud (with pinning);
- Device sends its certificate which was generated during enrollment.(?Https client-side authentication?);
- Cloud checks whether the certificate was enrolled;
- Cloud uses the TPM public key from the certificate and encrypts a CHALLENGE;
- Device receives the encrypted CHALLENGE and uses the TPM to decrypt it;
- Device generates a RESPONSE and encrypts it with the TPM;
- Device sends the encrypted RESPONSE to Cloud;
- Cloud decrypts it with the TPM public key, if it's ok, the authentication succeeded.
Benefits:
- TPM doesn't allow an attacker to gain access to Cloud, even if he or she was able to steal the private enrollment key (with a malware or forensic boot).
- We have the flexibility. For example, if we want to donate or sell the device, we can simply remove the enrollment key by device factory reset, or via Cloud web interface, if the device was stolen.
If you notice any mistakes or if you whould like to add anything, I will be happy to find your comment in Hackapp Facebook group or in any other place (plese leave link in comments).


I know, that not all devices are equipped with TPM chip (by the way, iPhone equipped), but I heard, that SIM card can be used, as TPM in some cases, if you know how it technical works, please let me know. phone spy software
ReplyDeleteCloud computing simply with a computer server capacity over the Internet. All that stuff is stored on the servers and you can use them and deal with them. Trendin
ReplyDeleteMore and more businesses are now taking advantage of the most powerful tool for higher success: cloud-based software and computing systems.
ReplyDeleteiDeals data room
Big data is the next big thing in the IT industry and it has created many job opportunities. Analysis of big data helps in making data driven decisions and to increase the profits of the business. Hadoop is the cloud based application which is used to analyse the big data.
ReplyDeleteBig data training in Chennai | Hadoop training in Chennai | angularjs training in Chennai
Hey, I appreciate to your writing.
ReplyDeleteTrue, I'm agreed with guys.
ReplyDeleteThx for writing, keep going!
Best regards
Toby, security online
Pretty Impressive and Interesting one guys, Keep going - AngularJS Training Institute in Chennai | Best AngularJS Training in Chennai | AngularJS training and placement
ReplyDeleteAnother trend likely to dominate the competitive landscape of the cloud storage gateway market in the coming years is that of partnerships between cloud storage suppliers and data security firms, offering a comprehensive suite benefitting both the service providers as well as the consumer.
ReplyDeletecompare cloud storage
Try out this gps spy tracking device anytime soon
ReplyDeleteRead about this hoverwatch keylogger and find out how you can easily monitor someone else's activity on any device.
ReplyDeleteRead more about my page with a lot of spy apps! https://spying.ninja/cell-phone-locator/
ReplyDeleteI know about a Snapchat spy app that can be used to monitor all activities like phone, messages, apps and more. If you want to spy on someone's mobile then it is a good app for this kind.
ReplyDeleteI know about a Snapchat spy app that can be used to monitor all activities like phone, messages, apps and more. If you want to spy on someone's mobile then it is a good app for this kind.
ReplyDeletehttp://www.mireview.com/snapchat-spy-app/
Secret pointing circuits
ReplyDeletemaxbet
แทงบอล maxbet
แทงบอล maxbet
Your blog is by far the best I have found.
ReplyDeleteทางเข้า maxbet
m8bet
สมัคร sbobet
Pretty post, really helpful to me. Keep up the good work and share more like this.
ReplyDeleteAngularjs Training institute in Chennai | Angular 4 Training in Chennai | Angular 2 Training in Chennai
If I ask, I will answer that I do not know how to think because it is floating.
ReplyDeleteIBCbet
I like your writing style, it was very clear to understanding the concept well; I hope you ll keep your blog as updated.
ReplyDeleteRegards,
Big Data Hadoop Training in Chennai|Hadoop Course in Chennai|Hadoop training institutes in chennai
It is a very informative blog for learning AngularJS. Thank you for sharing this wonderful blog.
ReplyDeleteAngular 4 Training in Chennai | AngularJS Training Chennai | AngularJS Courses in Chennai | Angular Training in Chennai
This is exactly what I wanted to read, hope in future you will continue sharing such an excellent article SEO Training Chennai
ReplyDeleteBest seo training in chennai
I have read all the comments and suggestions posted by the visitors for this article, very nice and waiting for your next article. Thanks!
ReplyDeleteweb designing institute in chennai
web designing training institutes in chennai
Generally, I don't make comments on sites, however, I need to say that this post really pushed me to do as such thing
ReplyDeleteFrench Language Classes in Chennai
French Training Institutes in Chennai
It is exceptionally valuable data. It will enhance my insight in Selenium. Much thanks to you for sharing this marvelous site.
ReplyDeleteSelenium training Chennai | Selenium testing training in Chennai | Best selenium training in Chennai | Selenium classes in Chennai
Good blog.Thankyou for sharing this good information..Python Training in Chennai
ReplyDelete
ReplyDeleteThankyou for sharing this good information.
hadoop training in chennai
Thanks for the blog and it is really very useful one.hadoop training in chennai
ReplyDeletehadoop training in bangalore
hadoop online training
hi, nice information is given in this blog. Thanks for sharing this type of information, it is so useful for me. nice work keep it up.
ReplyDeleteoutdoor led flood lights in delhi
Very informative post. Looking for this information for a long time. Thanks for Sharing.
ReplyDeleteTableau Training in Chennai
Tableau Course in Chennai
Tableau Certification in Chennai
Tableau Training Institutes in Chennai
Tableau Certification
Tableau Training
Tableau Course
Interesting blog, it gives lots of information to me. Thanks for sharing such a nice blog.
ReplyDeletepayrollmanagementservice
Article submission sites
Thanks for sharing,this blog makes me to learn new thinks.
ReplyDeleteinteresting to read and understand.keep updating it.
Android Courses in OMR
Android Training Institutes in T nagar
Best Android Training Institute in Anna nagar
best android training center in bangalore
Impressive Post!
ReplyDeleteJava Training in Chennai
Python Training in Chennai
IOT Training in Chennai
Selenium Training in Chennai
Data Science Training in Chennai
FSD Training in Chennai
MEAN Stack Training in Chennai
THANKS FOR INFORMATION
ReplyDeleteyou can search low-cost website with high-quality website functions.
Today Join Us
Call: +91 - 8076909847
website designing company in india
levantro
best interior designer in delhi
livewebindia
best website designing company in delhi
seo company delhi
Best It Service Provider:
1. Website Designing And Development.
2. SEO Services.
3. Software Development.
4. Mobile App Development.
This comment has been removed by the author.
ReplyDelete
ReplyDeleteIts such a wonderful arcticle.the above article is very helpful to study the technology thanks for that.
ccna Training Institute in Chennai
ccna Institute in Chennai
R Training in Chennai
R Programming Training in Chennai
Python Training in Anna Nagar
Python course in T Nagar
Good to read the article thanks for the author
ReplyDeleteTableau training in chennai
Reading this article is very useful
ReplyDeleteR training in chennai
You are doing a great job. I would like to appreciate your work for good accuracy
ReplyDeleteDotnet Training in Chennai
Dotnet Course in Chennai
Awesome article, I will never comment on other blog, but I will deeply read your article and I am collect many information with your article, thank you so much for share this valuable information with us, I really like to read this type blog, keep sharing like this type useful information am suggest to my all dear friend to visit this blog and get collect this great information, thank you so much for read my comment, if any one searching the website designing and also PPC company in India please come on my website ogeninfo system we are completed all type digital marketing in cheap rate.
ReplyDeleteWebsite Designing Company in India
I feel happy to say this I will deeply learning your blog and it’s really useful for me, keep sharing like this type valuable information regularly, I like to thanks for sharing this superb blog I hope I see you soon again time, thank you so much for read my comment, if any one searching the shipping company in India please visit my website yhcargoindia, we are shift your all type product with care in cheap rate.
ReplyDeleteCustom Broker in India
I am obliged to you for sharing this piece of information here and updating us with your resourceful guidance. Hope this might benefit many learners. Keep sharing this gainful articles and continue updating for us.
ReplyDeletemobile service center in velacherry
mobile service center in vadapalani
mobile service center in porur
HP Printer Customer Support Number
ReplyDeleteBrother Printer Support Phone Number
Canon Printer Customer Service Phone Number
Wonderful Post. Amazing way of sharing the thoughts. It gives great inspiration. Thanks for sharing.
ReplyDeleteXamarin Training in Chennai
Xamarin Course in Chennai
Xamarin Course
Xamarin Training Course
Xamarin Training in OMR
Xamarin Training in Porur
Xamarin Training in Adyar
Xamarin Training in Velachery
Norton phone number customer service
ReplyDeleteMcAfee support number
Malwarebytes customer support number
Hp printer support contact number
Canon printer customer support number
I am grateful to the owner of this site which really shares this wonderful work of this site. That is actually great and useful information. I would also like to share some useful information regarding SEO services in Delhi(www.nexcuit.com)This is the best SEO company in Laxmi Nagar, East Delhi. So if anyone is looking out for the Best SEO company in Delhi then reach out to them on the given number+919910326510 and get more details related to the packages they offer and their prices. One thing I can bet on is that you will get 100% satisfaction from there services.
ReplyDeleteseo services in delhi
best seo company in delhi
seo company in delhi
seo company in laxmi nagar
Nice post! I love this blog and I got more kinds of techniques in this topic. Thanks for your sharing.
ReplyDeletePrimavera Training in Chennai
Primavera Course in Chennai
Pega Training in Chennai
Unix Training in Chennai
Power BI Training in Chennai
Excel Training in Chennai
Oracle Training in Chennai
Social Media Marketing Courses in Chennai
Good Job. You have an in-depth knowledge. The way of sharing is very unique.
ReplyDeleteInformatica Training in Chennai
Informatica Training Center Chennai
Informatica course in Chennai
Informatica Training center in Chennai
Informatica Training chennai
Informatica Training institutes in Chennai
Informatica Training in OMR
Informatica Training in Porur
Looking for best TNPSC study materials to prepare for the examination? Make use of our samacheer kalvi books and other study guide to learn from experts. TNPSC One Time Registration
ReplyDeleteExcellent stuff, this is really helpful for beginners and I am glad to visit this page.
ReplyDeleteAWS Training in Chennai
AWS course in Chennai
VMware Training in Chennai
Vmware Training center in Chennai
Cloud Computing Courses in Chennai
Cloud Computing Training in Velachery
DevOps Certification in Chennai
AWS Training in Chennai
AWS course in Chennai
I am grateful to the owner of this site which really shares this wonderful work of this site. That is actually great and useful information. I would also like to share some useful information regarding digital marketing company in delhii(www.nexcuit.com)This is the digital marketing company in delhi located in Laxmi Nagar, East Delhi. So if anyone is looking out for the Best SEO company in Delhi then reach out to them on the given number+919910326510 and get more details.related to the packages they offer and their prices. One thing I can bet on is that you will get 100% satisfaction from there services.
ReplyDeletedigital marketing company in delhii
Best Digital marketing agency serving in Delhi
best digital marketing company in Delhi NCR
SEARCH ENGINE OPTIMIZATION (SEO)
Hello, I read your blog occasionally, and I own a similar one, and I was just wondering if you get a lot of spam remarks? If so how do you stop it, any plugin or anything you can advise? I get so much lately it’s driving me insane, so any assistance is very much appreciated.
ReplyDeleteData science Course Training in Chennai |Best Data Science Training Institute in Chennai
RPA Course Training in Chennai |Best RPA Training Institute in Chennai
AWS Course Training in Chennai |Best AWS Training Institute in Chennai
Devops Course Training in Chennai |Best Devops Training Institute in Chennai
Selenium Course Training in Chennai |Best Selenium Training Institute in Chennai
Advance Excel Training | Excel Training in chennai
Informative. It’s not easy to get such quality information online nowadays.Great going.
ReplyDeleteInplant Training in Chennai
Inplant Training
Inplant Training in Chennai for IT
Thanks for your article and sharing your expertise, it's really appreciated
ReplyDeletesmo company in delhi
social media marketing companies
social media agency in delhi
Thanks for your contribution in sharing such useful information. This was really helpful to me. Waiting for your further updates.
ReplyDeleteSpoken English Class in Anna Nagar
Spoken English Class in Porur
Spoken English Classes in T-Nagar
Spoken English Class in Adyar
Spoken English Classes in Chennai
IELTS Coaching in Chennai
IELTS Classes in Mumbai
English Speaking Classes in Mumbai
ReplyDeleteThanks for sharing Information to us.
cheap seo packages in delhi
seo packages
seo packages in india
On the off chance that you'd like to turn into an extraordinary author, it is important that you are an astounding peruser. Set aside the effort to truly peruse what you expound on, and appreciate it. When you can peruse it from a guest's perspective, you'll can show signs of improvement comprehension of any adjustments which you have to make for your composition style. opusbeverlyhills
ReplyDeletenice blog
ReplyDeletebest python training in chennai
best python training in sholinganallur
best python training institute in omr
python training in omr
python training in chennai
Is this can possible that any one hack my mobile?????????
ReplyDeleteBilaspur University BA 1st Year Result
BU BA Part 2 Result
Bilaspur University BA 3rd Year Result
Thank you for such a fabulous post. I have a lot of info and it is really helpful for developing my knowledge.
ReplyDeleteSpark Training in Chennai
Spark Training
Pega Training in Chennai
Primavera Training in Chennai
Unix Training in Chennai
Linux Training in Chennai
Social Media Marketing Courses in Chennai
Job Openings in Chennai
Placement Training in Chennai
Spark Training in Adyar
Thank you for this useful information
ReplyDeletepython training in chennai
php training
Such a confusing total with the general necessities of the sort of affiliation yours must be. There are two or three vivaciously express models they look at what's more. For example, each article that you course should have a page URL that contains a year. In like way, they need you to exhibit a news page guide spreads out a firm guide of where on your site or blog every story drives forward. Premium Blog
ReplyDeleteShould you have your own zone name similarly as your very own encouraging record, you will have substantially more open door in regards for the content you'll have the choice to post, and besides you won't run the hazard that your data will all evaporate in the event the host goes under! Outreach blog
ReplyDeleteChecking your inspiration can empower you to comprehend what sort of blog to set up and will reveal the get-together of observers you happen to need get. Both, are major zones of a sensational blog. Plan to use a photo show up inside your blog. People perceive to examine pictures. Endeavor and association with other related blog shows up over the web on improve your viewership. Top Guest Post Site
ReplyDeleteWonderful post and I hope you more updates from your blog. Thanks to you...
ReplyDeleteJMeter Training in Chennai
JMeter Training
Power BI Training in Chennai
Oracle Training in Chennai
Tableau Training in Chennai
Oracle DBA Training in Chennai
JMeter Training in Velachery
Hello dear admin, great post thanks for sharing, i really loved this. You’ve got some handy blogging skills I’ve Bookmarked your blog for future visit.
ReplyDeleteNetflix.com/nethelp code ui-800-3
Netflix com tvhelp
www Netflix com tvhelp
www Netflix com TVhelp for Guidance
Netflix com tvhelp
News blogs are the best wellspring of picked giving bits of getting some answers concerning any space of interest. There are unequivocal blogs proposed to cover present standard talking news, deciding and breaking news from around the world. These are ordinarily open on the web. With the PC being used for incredibly more than picking, you can find news sources saddling the power of this medium. You have different awesome to go online blog which give focused substance. online magazine
ReplyDeleteNice post, thanks for sharing. Great information worth reading. I’ve share this blog on my social media
ReplyDeleteOurTime Dating Site
How To Logout of Ourtime
Ourtime Login Password
Ourtime Dating Service
Our Time Dating Contact Number
Wow Nice post! Awesome & creative content, you’ve got some handy blogging skills. keep it up
ReplyDeleteVerizon Customer Service Phone Number
Verizon Customer Service Number
Verizon Customer Service
Bloggers generally pass on their thoughts and perspectives and what they feel about something and someone. There are numerous request and answer sessions that go on in a blog site. With a site, people are truly finding ways to deal with trade money making process. These days a critical number of the huge stars are truly making their own one of a kind blogs. Premium Blog
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteStrikingly sports fans are perhaps at an unfathomable good position. You can find the principle diversions channels on the web. Today you can watch international sporting events online with video spouting. Premium Blog
ReplyDeleteNevertheless, with such short period gazing us in the face the nonstop and long running advertisements on the TV can be very irritating and dull. Luckily, we by and by have the choice as news blogs that pass on the latest reports on current overall news and that too without the predictable advertisements! Outreach blog
ReplyDeleteWith this method, writers don't have to worry over their target advertise in light of the way that their structure will find it for them, for writing in a concentrated on route attracts perusers. Of course, there are as yet a huge amount of bloggers who select to go the other way and practice general blogging. Guest Post
ReplyDeleteBlogs are transforming into an extraordinary technique for sharing information with respect to any issue. As opposed to looking Google for general sites about a subject, one can go legitimately to a Blog in regards to the issue being alluded to and read each day examinations and contemplations by others with a comparable eagerness similarly as ace points of view. Online magazine
ReplyDelete
ReplyDeleteuncommon blog , keep it up Nice collection of information for us, Thanks.
Tinder help
Tinder customer service
How to use tinder
cancel tinder membership
Tinder refund
Such a great forum. Students will be able to find a list of more websites from
ReplyDeletethis post and they can learn better from these sites. Thanks for sharing the
post.
Hbogo com activate
hbogo com activate spectrum
hbo go activate firestick
www hbogo com activate
hbo go login activate
hbo go activate apple tv
hbo go activate ps4
hbo go activate device
Really I like your article it is easy to reading. You are a good blogger please keep it up. Thank you so much.
ReplyDeleteMatch com refund
match customer service
match com cancel
cancel match account
match com refund
cancel match com
how to delete match account
how to cancel match com
match.com help
match.com phone number
match com customer service number
A Tech Gadget lover…! Wanderlust of Nature by heart and a tech-savvy by habit.... I have written and reviewed blogs on many products. As a keen neophyte, I love to discover new Products and their plus points… Get in touch… Or drop in your queries.
ReplyDeleteMy blogs:
Roku.com/link
Roku.com/link create account
Roku.com/link account
Roku com link
Good..
ReplyDeleteINTERNSHIP IN CHENNAI FOR BCA
INTERNSHIP
INTERNSHIP FOR AERONAUTICAL ENGINEERING STUDENTS IN INDIA
INTERNSHIP FOR CSE 3RD YEAR STUDENTS
FREE INPLANT TRAINING COURSE FOR MECHANICAL STUDENTS
INTERNSHIP IN CHENNAI FOR ECE
INPLANT TRAINING FOR CIVIL
INTERNSHIP AT BSNL
INTERNSHIP FOR 2ND YEAR ECE STUDENTS
INTERNSHIP FOR AERONAUTICAL STUDENTS IN CHENNAI
This is one strategy for letting the peruser to consider the validity of the issue and the substances that support it. At some point or another, people will trust in the substance of the blog if all of the truths are there and all information shown has been had a strong reason and atmosphere. todaypost Blog
ReplyDeleteGlad to read your article. Nice collection of information for us, keep it up dear your blogs are very awesome .
ReplyDeleteSeeking Arrangement customer support
Seeking Arrangement customer service
Seeking Arrangement customer care
Seeking Arrangement phone number
A Tech Gadget lover…! Wanderlust of Nature by heart and a tech-savvy by habit... I have written and reviewed blogs on many products. As a keen neophyte, I love to discover new Products and their plus points… Get in touch… Or drop in your queries.
ReplyDeleteMy blogs:
Roku.com/link create account
Roku.com/link account
Roku.com/link activate
Roku.com/link activation
Roku.com/link activate account
Roku com link
Roku.com/link
Roku.com/link setup
very nice
ReplyDeletefreeinplanttrainingcourseforECEstudents
internship-in-chennai-for-bsc
inplant-training-for-automobile-engineering-students
freeinplanttrainingfor-ECEstudents-in-chennai
internship-for-cse-students-in-bsnl
application-for-industrial-training
Best Oracle Training in Chennai
ReplyDelete
ReplyDeleteA great post and a very explicit information.Thanks for this, such a very interesting
Update Garmin
Update Garmin gps
Update Garmin Maps
Update Garmin How to
The printer experts team provides troubleshooting services to HP printer users. They are available 24/7 to pick up your phone call.
ReplyDeleteHP Printer Support, Canon Printer Support, HP Printer Support Number
This comment has been removed by the author.
ReplyDeleteThey blog about the latest products accessible, what their business is about, and the services they offer. Blogs can be a great marketing instrument too. A few people blog to have any kind of effect in the world. These blogger blog about certain political issues and causes that can have any kind of effect in different people groups lives. The blog space additionally considers an examination between products offered by various companies. Online magazine
ReplyDeleteI am a technical writer based in Tampa, USA and I have been writing blogs on many technical products that have impressed me so far. When it comes to streaming, I have explored a lot of devices. But I have never come across a product like Roku.
ReplyDeleteMy blog:
Roku.com/link
Roku.com/link create account
Roku.com/link activate account
Roku.com/link account
Roku.com/link activation
Roku.com/link activate
Roku.com/link setup
www.Roku.com/link
Roku com link
Roku com link activation code
I like the helpful info you provide in your articles. I’ll bookmark your weblog and check again here regularly. I am quite sure I will learn much new stuff right here! Good luck for the next!
ReplyDeleteWeb Designing Course in Chennai | Web Designing Training in Chennai
Mobile Application Development Courses in chennai
Data Science Training in Chennai | Data Science courses in Chennai
I absolutely love that it looks so beautiful on you This is a great post it was very informative. I look forward in reading more of your work. Also I made sure to
ReplyDeletebookmark your website. I enjoyed every moment of reading it
pay suddenlink bill online
suddenlink bill payment
suddenlink bill pay
suddenlink pay bill online
pay my suddenlink bill
Dispersing your own one of a kind blog is basic and there are two distinct ways you can go. The first incorporates uniting with a free blog service. This takes not actually two or three minutes and once your record is opened, your blog can go live. Really, it genuinely is that essential and the free records have prepared it to be basic and accessible to all. Premium Blog
ReplyDeletePerfect post.
ReplyDeletepalm beach island tree service
Nice shared.
ReplyDeletekitchen remodel west palm beach fl
Nice blog. kitchen remodel parkland fl
ReplyDeleteThanks for sharing.
ReplyDeletekitchen and bath remodeling broward county
The latest technology blogs are formed by experts in various progressions. A blog is the place veterans in relevant fields write to share their understanding and as needs be, blogs on technology can be trusted for information on technology. Phones
ReplyDeleteSuch a superb post shared.
ReplyDelete24 hour air conditioning repair west palm beach
Nice post.
ReplyDeletekitchen and bath remodeling broward county
Thanks for sharing.
ReplyDeletedigital water heater jacksonville
Great posting.
ReplyDeletekitchen and bath remodelers fort lauderdale
Nice post.
ReplyDeletekitchen and bath remodelers wesley chapel
I read your content it seems to be a very good looking and a uncommon content , thanks for sharing this content dear
ReplyDeleteHbogo com activate
hbogo com activate spectrum
hbo go activate firestick
www hbogo com activate
hbo go login activate
reactivate hbo go
hulu.com activate my device
hulu.com/activate enter code
hulu-password-reset
hulu-com-forgot
hulu com activate
hulu.com/activate not working
Great Post!
ReplyDeletehow to set up roku
how to set up roku on tv
how to set up roku stick
how to setup roku streaming stick
how to set up a roku streaming stick
how to set up roku streaming stick On Smart TV
ReplyDeleteHello! Would you mind if I share your blog with my zynga group?
There’s a lot of folks that I think would really appreciate your
content. Please let me know. Cheers
xfinity.com/activate
Then again, with the current worldwide financial down-turn, where almost every other specialist isn't really certain about whether they'll be receiving walking papers or adequate hours, it's not really an awful idea to think money and mull over an online business and starting up a daily blog. marketing
ReplyDeleteAs said before, Finance is a gigantic subject with numerous classes. Indeed, even before beginning your blog composing, settle on what classification you need to compose. Also, significantly increasingly significant is to adhere to it. This is significant on account of the nearby between connection of these classifications that can undoubtedly divert you to an alternate class all together, and without your insight. For eg. You may begin composing 'On the best way to deal with your Personal Finance'. There comes one pivotal point in it about reimbursing your high need obligations. Here you can without much of a stretch wind up expounding more on that and disregard different purposes of planning. HELPWITHFINANCE
ReplyDeleteAn impressive share! I've just forwarded this onto a co-worker who had been conducting a little research on this. And he in fact ordered me breakfast because I found it for him... lol. So let me reword this.... Thank YOU for the meal!! But yeah, thanks for spending the time to discuss this subject here on your site.
ReplyDeletehttps://kbcgameshow.biz/
Really Nice Post! Thanks for Sharing this this amazing post its really helpful.
ReplyDeleteXfinity Pay Bill, Xfinityn Bill Pay, How to make xfinity pay bill, How to get rid of xfinity pay my bill, How to make xfinity online payment
Life is so involved and it creates the impression that standard speaking, things kind of stack up on us. We may have a whole arrangement for the day that just keeps creating since we don't make the chance to ever do them. Conventionally we think about gigantic exercises to do, anyway every so often, it's the little broadens that can give us a commencement. Home improvement tips can be as fundamental as taking one room on the double and dealing with it. HomeImprovementNews
ReplyDeleteRight when blog writing, you have to guarantee that your grammar and spelling is incredible. As people, we are not incredible and we have an allowance for a couple of bumbles. Regardless, in case someone reads a blog that has many spelling and grammar mistakes after one another statement, they won't come back to read it. Thedailymint News
ReplyDeleteNice infromation
ReplyDeleteקבוצת גבאי
I think the Cloud storage is one of the best inventions! Just like spy software for cell phones! It can be useful for everyone - parents, employers, spouses! Please read more about it!
ReplyDeleteIt’s my first time to visit this site & I’m really surprised to see such impressive stuff out there Good information here. I really enjoy reading them every day. I’ve learned a lot from them.Thanks so much for sharing this information. Greatly help me being a newbie.
ReplyDeletemobile app services in Delhi NCR
Php Web Development Company in India
To start with, in the event that I can say, perusing the models you referenced in this blog is exceptionally motivating. Much obliged to you for making this rundown.
ReplyDeleteWww HBO Go Com Activate
hbo now activate
hbo go sign in
hbo gotv sign in
hbogo comactivate and enter this code
hbo gotv code
hbo go app
hbo go account
xfinity hbo go
hbogo com activate
hbogo com/activate
hbogo..com/activate
hbogo/com/activate
hbogo. com/activate
hbogo com activate
hbogo activate
hbogo/activate
hbogo com activate
hbogo activate
hbogo login
hbogo/tvsignin
hbogo,com/activate
hbogo/activate.com
hbogo sign in
hbogo..com/activate
hbogo com/tvsignin
His article is so convincing that I never stop talking about it. You are doing a great job.
ReplyDeleteKeep it up!
But we also provide The Wish customer service, if you have any problems, you can contact us.
Delineate a strong character. Writing blogs is consistently done in the fundamental individual viewpoint and this gives you an opportunity to tell others the kind of character you have. To do this right, confirm you develop a strong impression. Sound capable on what you're talking about considering the way that as you do, you build your master in a particular field too. You can't attract a reader for long if you can't show the individual being referred to that you merit listening to. Thelivejournal Blog
ReplyDeleteThere are a couple of tips gambling bloggers can use to assemble their chances of benefitting on the web. These tips are not so much chooses that must be painstakingly sought after yet they come way in helping money gambling bloggers especially the people who are new to fabricate their chances of making money gambling blogging. gamblebest casino
ReplyDeleteChildren must be stimulated by the gatekeepers and instructors to make their own blogs constantly. Online education blogs, other than the networking websites, is considered to accept an imperative employment in motivating children to make. Audits reveal that students who don't ordinarily get to online education blogs have shown lesser writing capacity and improvements than the people who have their own special blogs. With better execution in schools, the children, referring to online education blogs are showing more energy for writing. This is again valuable in structure their sureness, helping them to surpass desires in writing. Learning
ReplyDeleteGreat Article
ReplyDeleteData Mining Projects
Python Training in Chennai
Project Centers in Chennai
Python Training in Chennai
hbogo.com/activate to activate HBO GO on your Roku Streaming Stick. We provide help for HBO GO activate process.
ReplyDeleteWww HBO Go Com Activate
hbo now activate
hbo go sign in
hbo gotv sign in
hbogo comactivate and enter this code
hbo gotv code
hbo go app
hbo go account
xfinity hbo go
hbogo com activate
hbogo com/activate
hbogo..com/activate
hbogo/com/activate
hbogo. com/activate
hbogo com activate
hbogo activate
hbogo/activate
hbogo com activate
hbogo activate
hbogo login
hbogo/tvsignin
hbogo,com/activate
hbogo/activate.com
hbogo sign in
hbogo..com/activate
hbogo com/tvsignin
Routinely, we see something in a headway and worship it, in any case after really viewing the thing truly, we start to see the anomalies. In reality viewing the things spares us from submitting tremendous mistakes. It likewise empowers us set aside an enormous measure of money that we may have normally spent. Online shopping blogs should reproduce a relative power for customers all over on the Internet. shopping bloggen
ReplyDeleteNext, you need to skirt Blog Post that foresee that you should utilize kitchen hardware you don't have, except for if you can get the machine from a sidekick. You can't make waffles with hand made set yogurt or custard on top in the event that you don't have a waffle iron. Basically add the waffle iron to your Christmas summary and proceed ahead. There are incalculable recipes accessible, so don't get hung up on one you are not set up for gathering.
ReplyDeleteהייתי חייבת לפרגן, תודה על השיתוף.
ReplyDeleteקבוצת גבאי בעלים
This comment has been removed by the author.
ReplyDeleteGreat Article.
ReplyDeleteפרגולה מאלומיניום
Your content is very rare and its words are so impressive so keep on sharing more content with us like this for more information : Www Roku Com Link
ReplyDeleteLink Code Roku
Roku Com Link Activate
Roku Com Link Activation
Roku Com Link Enter Code
Roku Com Link
Ruko Com Link
i love your article.
ReplyDeleteמעקות אלומיניום
כל מילה. תודה על השיתוף, מחכה לעוד פוסטים בנושא.
ReplyDeleteטבעת יהלום
לגמרי פוסט שדורש שיתוף תודה.
ReplyDeleteרהיטים לסלון
כתיבה מעולה, אהבתי. אשתף עם העוקבים שלי.
ReplyDeleteמגשי אירוח מתוקים
פוסט נחמד. חייב לשתף עם העוקבים שלי
ReplyDeleteשולחן עגול נפתח
תמשיכו בפרסום פוסטים מעניינים כמו זה. תודה.
ReplyDeleteטיפולים קוסמטיים
רציתי רק לשאול, אפשר לשתף את הפוסט בבלוג שלי?
ReplyDeleteשולחן אוכל
Very informative post.
ReplyDeleteמערכות קול
keep posting.
ReplyDeleteעמוד לטלוויזיה
הדעות שלי קצת חלוקות בעניין הזה אבל ללא ספק כתבת מעניין מאוד.
ReplyDeleteארגון חתונה
תמשיכו בפרסום פוסטים מעניינים כמו זה. תודה.
ReplyDeleteבייביזמול
פוסט מעניין, משתף עם העוקבים שלי. תודה.
ReplyDeleteהשקעה בנדלן בארץ
Thanks for sharing this beautiful information with us your content is really amazing, thanks for sharing it.
ReplyDeletenetflix com loginhelp
netflix com activate enter code
netflix com activate code tv
how to get activation code for netflix
Thanks for giving great kind of information. So useful and practical for me. Thanks for your excellent blog, nice work keep it up thanks for sharing the knowledge.
ReplyDeleteTour and Travel agents in Delhi NCR
Best Tour Operator in India
I have to voice my passion for your kindness giving support to those people that should have guidance on this important matter.
ReplyDeletesalesforce admin training in bangalore
salesforce admin courses in bangalore
salesforce admin classes in bangalore
salesforce admin training institute in bangalore
salesforce admin course syllabus
best salesforce admin training
salesforce admin training centers
great post.
ReplyDeleteפלאנרז הפקות
Hello author this is one of the best blog I've come across lately thanks for making such a beautiful post
ReplyDeleteNetflix.com/nethelp code ui-800-3
Netflix com tvhelp code nw 8 17
www Netflix com tvhelp for guidance
Netflix com tv help
www Netflix com help tv
www netflix com loginhelp
netflix com activate
netflix activate
מזל שנתקלתי בכתבה הזאת. בדיוק בזמן
ReplyDeleteמערכת מצלמות אבטחה
Thanks to you that i managed to find the solution of the issue in your blog. The article have explained the solution in the simplest way possible.
ReplyDeleteTinder Customer Service ,Tinder Technical Support ,Tinder Support Phone Number ,Tinder Tech Support ,Tinder Technical Support ,Tinder Support ,Cancel Tinder Subscription ,How to Cancel Tinder ,Cancel Tinder ,How to Cancel Tinder Account ,Cancel Tinder Subscription ,Tinder Login Error ,Tinder Login Problems ,Tinder Login Problem ,Tinder Customer Support ,Tinder Customer Care ,Tinder Toll Free ,
If you are also the one who want to keep updated on the latest development in technology, must follow your blogs.
ReplyDeleteHow to cancel match,Cancel match,Cancel match com,How to cancel match com,How to use match com without paying,Match phone number,Match com refund,Match customer service,
Great blog it its really informative and innovative keep us posted with new updates. It was really valuable. Thanks a lot.
ReplyDeleteBest Lawyers in Delhi NCR
Civil Lawyers in Delhi
Best Family Lawyer in Delhi
Great post very nice.
ReplyDeleteשולחן עגול נפתח
I am reading this publication, your publication is very good and very informative. Thanks for sharing this post.
ReplyDeletewww netflix com
netflix gift card
netflix com payment
netflix com activate
netflix not working
netflix help
netflix activate
www netflix com login
help netflix com
netflix com account
netflix rom coms
www netflix com redeem
netflix com proxy
netflix com redeem
netflix com sign in
netflix com tvhelp
netflix not working on roku
rom com netflix
www netflix com help
https www netflix com
netflix com nethelp
pname com netflix mediaclient
why is netflix not working
www netflix com activate
best rom com on netflix
netflix com clearcookies
netflix com login
netflix com tv
netflix not working on smart tv
www netflix com loginhelp
www netflix com tvhelp
Thankyou for this article this information is very useful for me. i have also information for you A list of the best ACP sheets and acp sheet manufacturers in India who produces compact, strong and durable sheets those are best for your home décor, office or Industry etc. Aluminium
ReplyDeleteComposite Panel
Thank you for sharing this fantastic blog, really very informative. Your writing ability is very good, you should continue to write this type of blog.
ReplyDeleteWWW Netflix Com
Netflix Activate
Netflix Com Activate
WWW Netflix Com Activate
Netflix Activation Code
Netflix Active Accounts
Activate Netflix Com Your Account
Netflix.com/Activate
WWW Netflix Com login
Nice Blog, Most Of Us Work To Live Our Lives, Yet We Still Want To Do Things That Don’t Feel Like Work"
ReplyDeleteBe It Teaching Or Learning, The Joy Is In Being Connected. MillionCenters Aims To Bridge The Gap Between Learners And Tutors With A Technology-Based Online Platform.
ReplyDeleteYou have provided an nice article, Thank you very much for this one. And i hope this will be useful for many people.. and i am waiting for your next post keep on updating these kinds of knowledgeable things...
Selenium Training in Chennai
I am your customer who had encountered the administrations by you half a month prior. I am really happy with the administration you offered to me. Here I am simply to state thank you for offering the best administrations. I couldn't imagine anything better than to team up with your in not so distant future.
ReplyDeleteAmazon Fire Stick Troubleshooting, Amazonfire Stick Troubleshooting, Fire Stick Troubleshooting, Firestick Troubleshooting, Amazon Firestick Troubleshooting, Firestick Troubleshooting, Fire Stick Troubleshooting, Firestick Problems
Nice Article, Get the latest mutual fund investment schemes and performance of the mutual fund schemes. For any fire stick issue visit us..
ReplyDeleteFire Stick Controller Not Working ,Amazon Fire Stick Customer Service ,Amazon Fire Stick Reset ,Fire TV Not Working ,Fire Stick Not Working ,Fire Stick No Signal ,Amazon Fire Stick No Signal ,Firestick Reset Itself ,Amazon Fire Stick Reset Itself
I wanted to thank you for this great read!! I definitely enjoying every little bit of it I have you bookmarked to check out new stuff you Post , For any verizon pay bill issue visit us..
ReplyDeleteVerizon Pay My Bill ,Verizon Pay My Bill ,Wireless Verizon Pay Bill ,Verizon Pay Bill Phone Number ,Verizon Pay Bill Online ,Verizon Pay Bill Phone ,Verizon Pay Bill Online Login ,Verizon Pay Bill Online One Time ,Verizon Pay Bill Online Residential ,Verizon Pay My Bill ,Verizon Pay My Bill ,
Satta King
ReplyDeletenice site
Satta King
ReplyDeleteosm site
how do i cancel pandora, pandora subscription cancel, how to cancel my pandora subscription, cancel pandora subscription, how to.cancel pandora subscription, how to cancel pandora subscription, how to cancel a pandora subscription, how to cancel.pandora subscription, how do i cancel my pandora subscription, cancel my pandora subscription, how to cancel pandora subscription on iphone, how do i cancel pandora subscription, cancel pandora plus subscription,
ReplyDeleteReally informative information..... Thanks for sharing this post.. My work exists at the intersection of Mobile development and technology blogging. If you are looking for Mobile app Development help then Great Mobile app Company Help is always ready to help their customers at affordable prices. To gather more information, inbox us or browse our web pages at any time.
ReplyDeleteMobile application development Companies in Dubai
Awesome port bro, you really explained everything neatly. actually, i am new and thus was eager to know more about TF and CF, thanks to your providing such an awesome Post, For any HP Printer issue visit us..
ReplyDelete1(888)-823-4450,http://123.hp.com,http://123.hp.com/setup,123.hp.com app,hp.com/123,hp/com/123,www,hp,com/123,HP Printercom/123,123-hp-com,123 HP Printercom setup,123-hp-com,123 HP Printercom setup,hp,com/123,123 HP Printercom setup,hpcom123,123comhp,123hpcom,123 hp.com,123.HP Printercom,HP Printercom 123,HP Printer123 com,123 HP Printercom,hp.com.123,hp.123.com,123.hp.com,1(888)-823-4450
After looking into a number of the blog articles on your web site, I honestly like your technique of blogging. I saved it to my bookmark site list and will be checking back soon. Please visit my web site as well and let me know how you feel. Jio Lottery Winner 2020
ReplyDeleteThanks for sharing this beautiful information with us. Keep in sharing more and more updates on this types of information.
ReplyDeletecancel pandora
cancel pandora subscription
how to cancel pandora
how to cancel pandora subscription
how to cancel pandora plus
cancel pandora plus
As a full-service payment processor, we can provide the beyond secure hardware and software your organization needs to accept both online and mobile payments. Moreover, as a globally respected brand, we can help your company expand its volume and profitability by processing transactions from customers based all over the world. We got our high risk merchant account from premieronepayments.com
ReplyDeleteThe markets are starting to take off like wildfire, but we are still in the early stages of this industry and businesses that know how to market and advertise are going to be the ones that capitalize on this extreme growth the most. cbd oil marketing online
ReplyDeleteHdmovieshub
ReplyDeleteI really like your blog very much. And i will post it on my social media sites. Keep on updating more details about it. Thanks for the post.
ReplyDeletepandora cancel subscription
how do i cancel pandora
pandora cancel
הדעות שלי קצת חלוקות בעניין הזה אבל ללא ספק כתבת מעניין מאוד.
ReplyDeleteמציאות רבודה
Thanks for this post
ReplyDeleteglobal asset management
Great posting.
ReplyDeleteglobal asset management
Also known as the Yemen chameleon, the veiled chameleon is originally from the mountain ranges and valleys in Saudi Arabia and Yemen. Their natural habitats within the coastal mountain ranges have lots of rain, and the slightly drier valleys they reside in have plenty of water and vegetation all year. chameleon care
ReplyDeleteOne thing you should know is that you can never pick up money when playing bandar judi online if you don't understand what it is about. That is the explanation you should contribute some centrality learning the stray pieces and systems you can use before playing Togel games. Through this move, it won't take some time before you maximize your winning without pushing. bandar judi online
ReplyDeleteWhen we started the Top Bamboo Products blog, our aim is to bring the usage of bamboo closer to other people. We go beyond the typical knowledge many know about bamboo. We dig deep to show that the bamboo plant is more than its construction material value. bamboo extract
ReplyDeleteDigital Marketing Services in Chennai
ReplyDeleteSEO Company in Chennai
SEO Consultant Chennai
CRO in Chennai
PHP Development in Chennai
Web Designing Chennai
Ecommerce Development Chennai
Concerning achieving success in the digital space, the experience and professionalism of SEO agencies in Singapore will matter a ton. If you want to give indications of improvement return on your investment, you need to pick an agency having a considerable experience in dealing with businesses in your industry. SEO agencies in Singapore
ReplyDeleteI know the value of Garmin Update and keep reading good content about the same. I found this blog very informative and it increased my understanding about garmin update to a great extent.
ReplyDeleteAmenities at TATA Promont include a fully equipped clubhouse, landscaped gardens, gymnasium, swimming pool, recreation rooms, outdoor sports courts, children’s play area, party hall, and meticulously planned with utmost importance to state-of-the-art 24/7 securities. tata promont price
ReplyDeleteดูหนัง พบกับหนังออนไลน์ที่คมชัดเต็มระบบ ทั้ง 4K HD สนุกง่ายๆ กับ Can You Keep a Secret? คุณเก็บความลับได้ไหม? (2019)
ReplyDeleteEven if you are not sure of what you want, our e-shop has got several ways to help you identify your needs. Everything about Posturefixer30 revolves around our commitment to help you look your best and inspire confidence in you. posture corrector
ReplyDeleteWithout a doubt, having a Will written is important. However, unlike a Will, a Trust can serve many purposes to complete estate planning. For instance, a Trust allows wealth protection and preservation which a Will cannot do. setting up a trust in Singapore
ReplyDeleteRoku is all about media streaming or brings media from the internet. And Roku com link is used to activate the Roku Streaming player or Roku Streaming Device. you towards the activation of your new mode of entertainment with all of your favorite channels, shows, movies, and dramas that you simply are looking forward to.
ReplyDeleteI am glad to read your well researched article. Your content is accurate and you have given the cream of the crop for your readers. Web Designing Course Training in Chennai | Web Designing Course Training in annanagar | Web Designing Course Training in omr | Web Designing Course Training in porur | Web Designing Course Training in tambaram | Web Designing Course Training in velachery
ReplyDeleteAwesome article! It is in detail and well formatted that i enjoyed reading. which in turn helped me to get new information from your blog. For any dating help please visit :
ReplyDeletecancel pandora subscription,how to cancel pandora subscription,pandora cancel subscription,how do i cancel my pandora subscription,how to cancel pandora subscription on iphone,cancel pandora,how to cancel pandora,how to cancel pandora plus,cancel pandora plus,how do i cancel pandora,how do i cancel my pandora subscription,how to unsubscribe from pandora plus,cancel pandora subscription,
הדעות שלי קצת חלוקות בעניין הזה אבל ללא ספק כתבת מעניין מאוד.
ReplyDeleteהדפסה על קנבס מחיר
Thanks for your sharing, it helps me a lot and I think I'll watch your post more.
ReplyDeleteאינטרקום לדלת כניסה
A best information provider, You are really doing well, please keep it up. Such a nice article i got more helpful information from here.
ReplyDeleteshein return policy||shein return policy usa||shein returns policy||shein refund policy||shein exchange policy||how do i return to shein
Before you begin to use Facebook for marketing, consider if you really have the time to pull it off. You'll need someone to post at least once per day, and then you'll need to include other features such as a Promotions tab or polls. thansk
ReplyDeleteAi & Artificial Intelligence Course in Chennai
PHP Training in Chennai
Ethical Hacking Course in Chennai Blue Prism Training in Chennai
UiPath Training in Chennai
Really great post. Students will be able to find a list of many sites from this post and they can learn a lot better from these sites. Thanks for sharing the post. For any Netflix Issue Visit US:
ReplyDeletenetflix com tvhelp ,netflix com tv help ,netflix com tv help ,www netflix com tv help ,netflix com tv help ,netflix com tvhelp ,netflix com tv help ,netflix com tv help ,netflix com tv help ,netflix com tvhelp ,n8106 154 5003 ,Error 5003 Netflix ,Netflix Com Activate ,Netflix Password Reset ,Netflix Error Code 5003 ,Www Netflix Com Activate ,Netflix Activate ,Netflix.Com/Activate ,Www Netflix Com Activate ,Www Netflix Login Issue ,Netflix Login Problems ,Netflix Not Working ,
Very good publication, I like similar publications. Thank you for sharing the information.
ReplyDeletemcafee activate
mcafee/activate
www mcafee activate
mcafee com/activate
activate mcafee
Nice article and best information for me. I am proud of you admin pls keeo it up and if any customer facing any problem by dating website then please visit our website:
ReplyDeleteHow to Cancel Match Subscription,Cancel Match Subscription,How Do I Cancel My Match Subscription,How to cancel match,cancel match,How to cancel match.com,Match Com Cancel Membership,Match Com Cancel,Cancel Match Account,Cancel Match Com Subscription,HCancel Match Membership,Match phone number,Match com refund,Match customer service,Match.com refund,Match refund,Cancel Match,Match.com cancel
This is really great work. Thank you for sharing such a good and useful information here in the blog for students. For any Tinder Account Problem Visit US:
ReplyDeletetinder refund, tinder gold refund ,refund tinder gold, how to get a refund for tinder gold , tinder plus refund , how to refund tinder gold , how to get a refund on tinder , how to get a refund from tinder , how to get tinder refund , Tinder Customer Service , Tinder Phone Number ,Tinder Support
Tinder Customer Service ,Tinder Technical Support ,Tinder Support Phone Number ,Tinder Tech Support ,Tinder Technical Support ,Tinder Support ,get tinder refund ,How to Cancel Tinder ,Cancel Tinder ,How to Cancel Tinder Account ,get tinder refund ,Tinder Login Error ,Tinder Login Problems ,Tinder Login Problem ,Tinder Customer Support ,Tinder Customer Care ,Tinder Toll Free
What's on sale today? Get exciting offers on sanitizing devices! Most people buy sanitizers that are based on other factors such as design, scent, pet and kid-friendliness, etc. This article will serve as a Complete Guide For Sanitizing Your Device
ReplyDeleteGreat work. Thank you so much for sharing this such a nice information here in the blog for visitors.
ReplyDeleteSilverSingles technical Support phone Number,Silver Singles toll free number,SilverSingles customer care,Silver Singles Phone number,Silver Singles tech Support,Silver Singles customer support,SilverSingles customer service,Silver Singles support phone number,Silver Singles tech Support Number,SilverSingles Login Problem,Silvesingles Support,Silve singles customer service,Silvesingles customer service number,SilverSingles help,Cancel silversingles membership,Silvesingles refund,Silvesingles delete account,Silvesingles cancel subscription,Silve singles customer care,Silve singles support number,How to create Silve singles account,How do i cancel my silver singles membership,How to create Silve singles account,SilverSingles Login Problem,SilverSingles Forgot Password,Silvesingles email notification
Your blog is amazing, all the content is really unique and useful. Thank you for sharing this with us.
ReplyDeletehow to activate mcafee antivirus
mcafee activate enter code
www mcafee com activate
mcafee./activate
mcafee activate product
Much thanks to you such a great sum for this instructional exercise! I've been scanning for a strong one for quite a while and yours was incredibly helpful. For Cashapp Help visit:
ReplyDeleteHow to Change Password With Cash App Account , How to Recover Cash App Forgot the Password, How to Reset Cash App Pin , How to send bitcoin to cash app , Delete Cash App Account, Cash App Not Working, How to Contact Cash App Refund Support, How to Delete Cash App Account , Cashapp login problems , Cash App Reset Pin , Reset Cash App Pin , Cash App Refund , Get Cash App Refund , Change Cash Password , Cash App Customer Service , Cash App Customer Support Number ,
Much thanks to you such a great sum for this instructional exercise! I've been scanning for a strong one for quite a while and yours was incredibly helpful. For Cashapp Help visit:
ReplyDeleteHow to Change Password With Cash App Account , How to Recover Cash App Forgot the Password, How to Reset Cash App Pin , How to send bitcoin to cash app , Delete Cash App Account, Cash App Not Working, How to Contact Cash App Refund Support, How to Delete Cash App Account , Cashapp login problems , Cash App Reset Pin , Reset Cash App Pin , Cash App Refund , Get Cash App Refund , Change Cash Password , Cash App Customer Service , Cash App Customer Support Number ,
awesome post.
ReplyDeleteglobal asset management korea
Opting for eyebrow embroidery Singapore is unquestionably going to improve your outward introduction. Regardless, you have to promise you are relying on professionals to get the look you so desire. To save you from the stress of looking at apparent service providers out there, it is better to interface with La Vida. classic eyebrow embroidery
ReplyDeleteWith such huge degrees of companies out there offering private safe deposit boxes, you may feel that its hard in choosing the best. To make your quest direct, you ought to consider opting for UltraVault Safe Depository services. With more than 50 years of experience in the industry, you will never regret your decision of working with UltraVault. safe deposit box Singapore
ReplyDeleteThis is extremely incredible work. Much obliged to you for sharing such a decent and helpful data here in the blog for understudies. For any Cash App Card Issue Visit US:
ReplyDeleteActivate Cash App Card,How to Activate Cash App Card,How to Change Password With Cash App Account ,Cash App Activate Card,How Do I Activate My Cash App Card,Cash App Help Activate Card,Reset Cash App Pin,Delete Cash App Account,Cash App Login Problems,